Multifactor authentication (MFA)
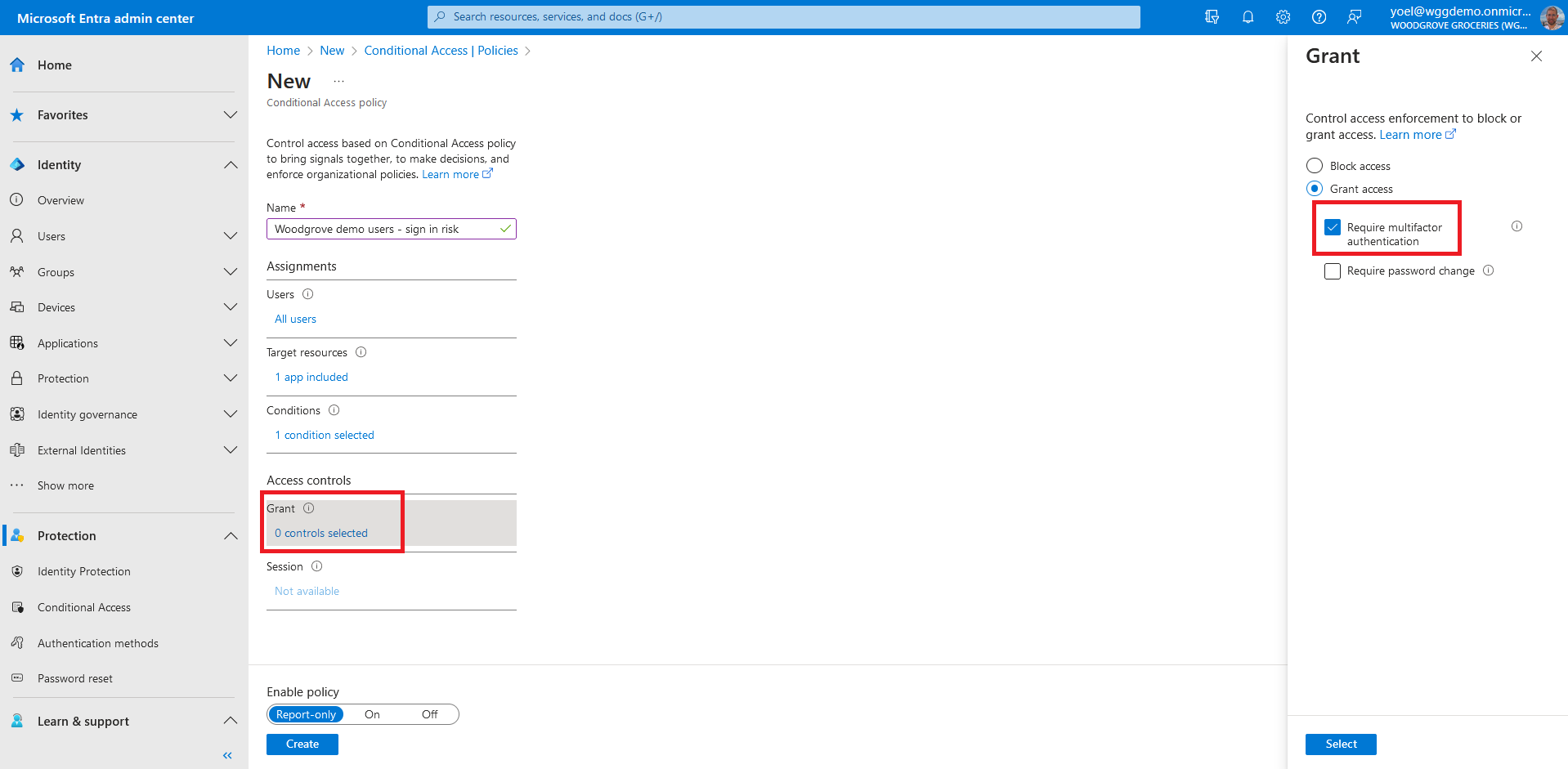
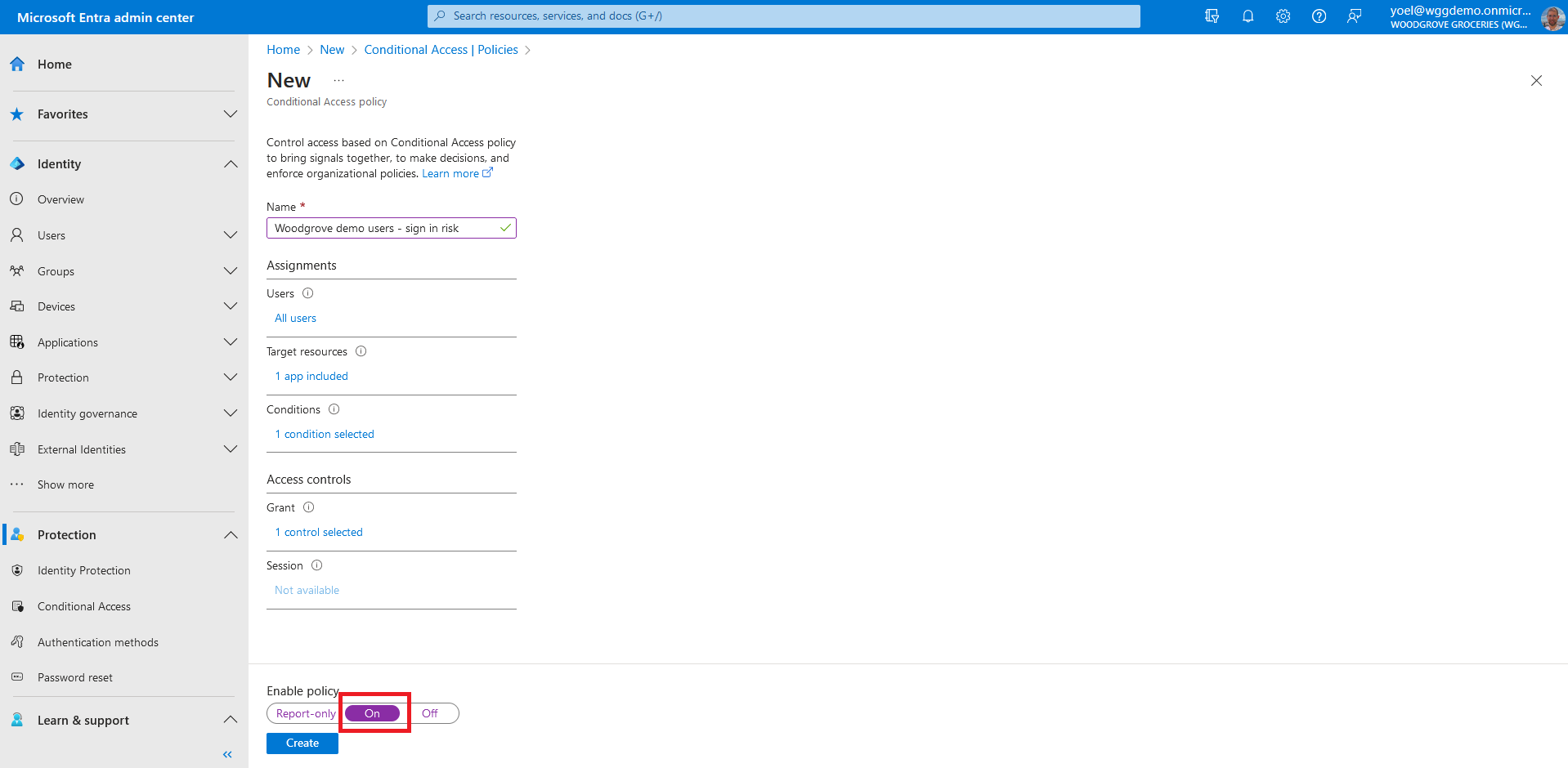
Multifactor authentication (MFA) protects customers identity by prompting them for a second verification method. Microsoft Entra Conditional Access brings signals together, to make decisions, and enforce security policies. In this demo shows a Conditional Access policy that prompts for MFA. The Conditional access policy targets all users without any condition.
Prerequisites
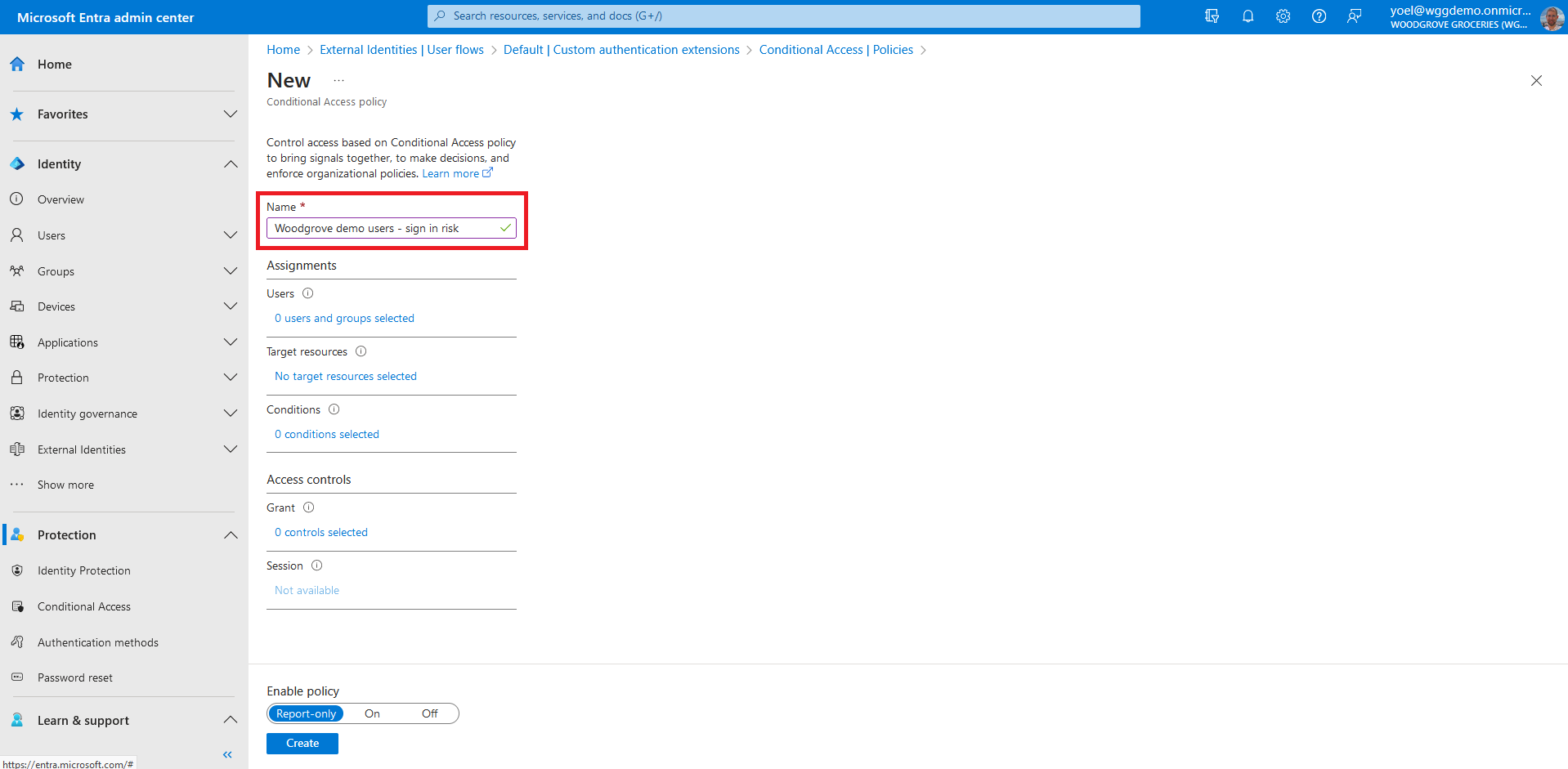
Before you start make sure you have configured the following:Start by creating a Conditional Access policy to secure the application. Sign in to the Microsoft Entra admin center and browse to Protection > Conditional Access. Then, select New policy.
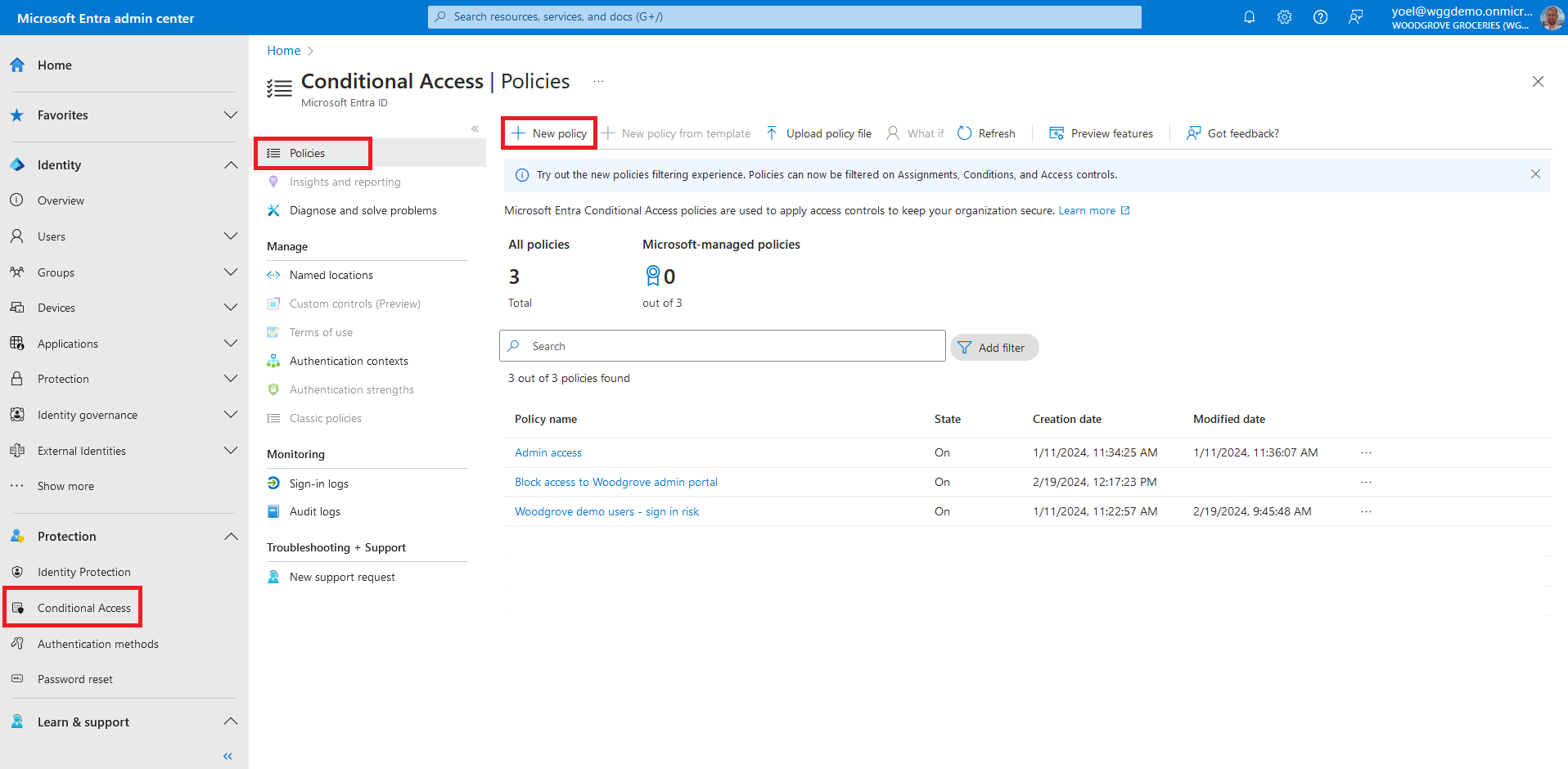
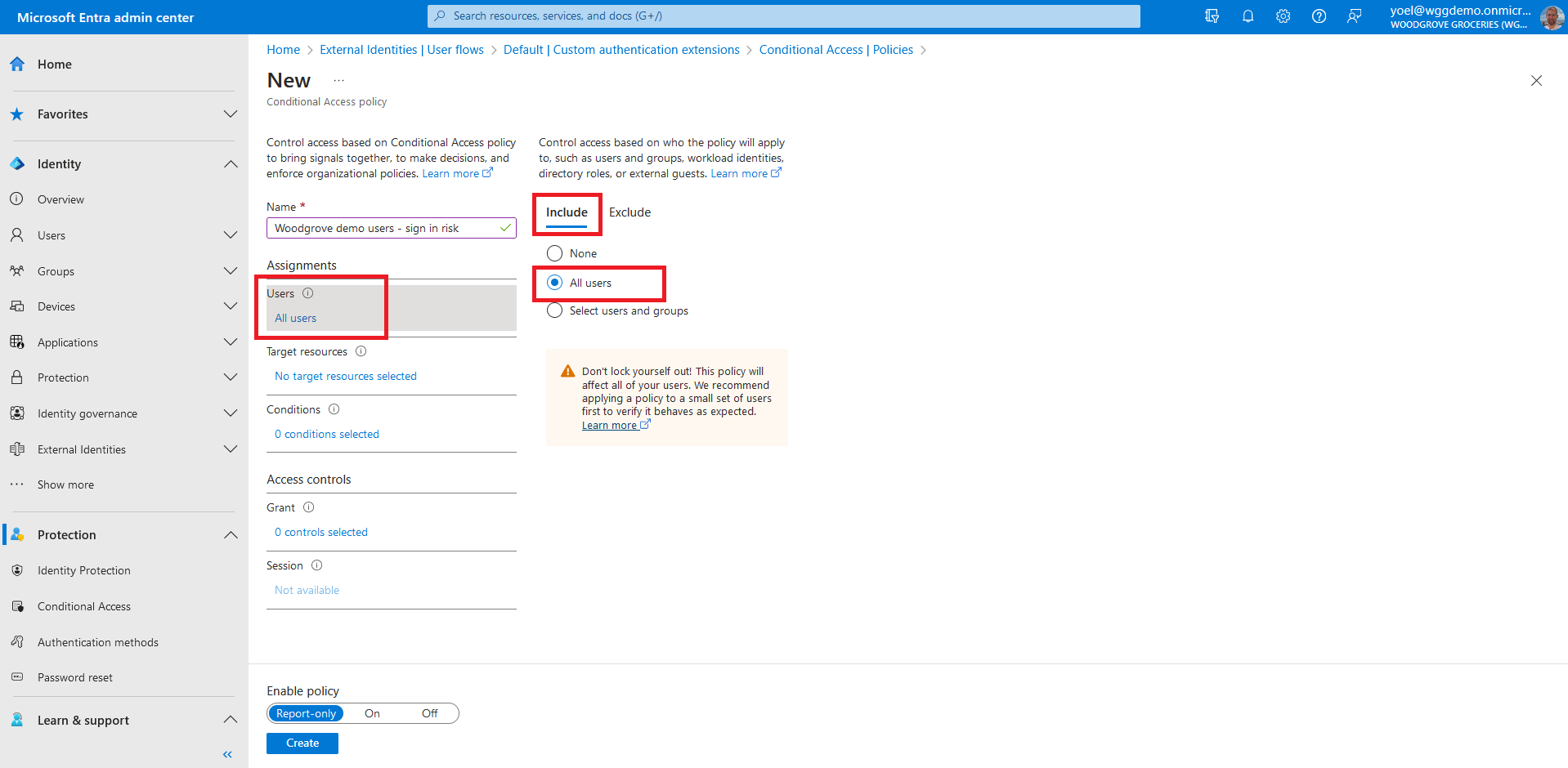
Under Assignments, select the link under Users. Then, on the Include tab, select All users. On the Exclude tab, you can select users and groups for your organization's emergency access or break-glass accounts.
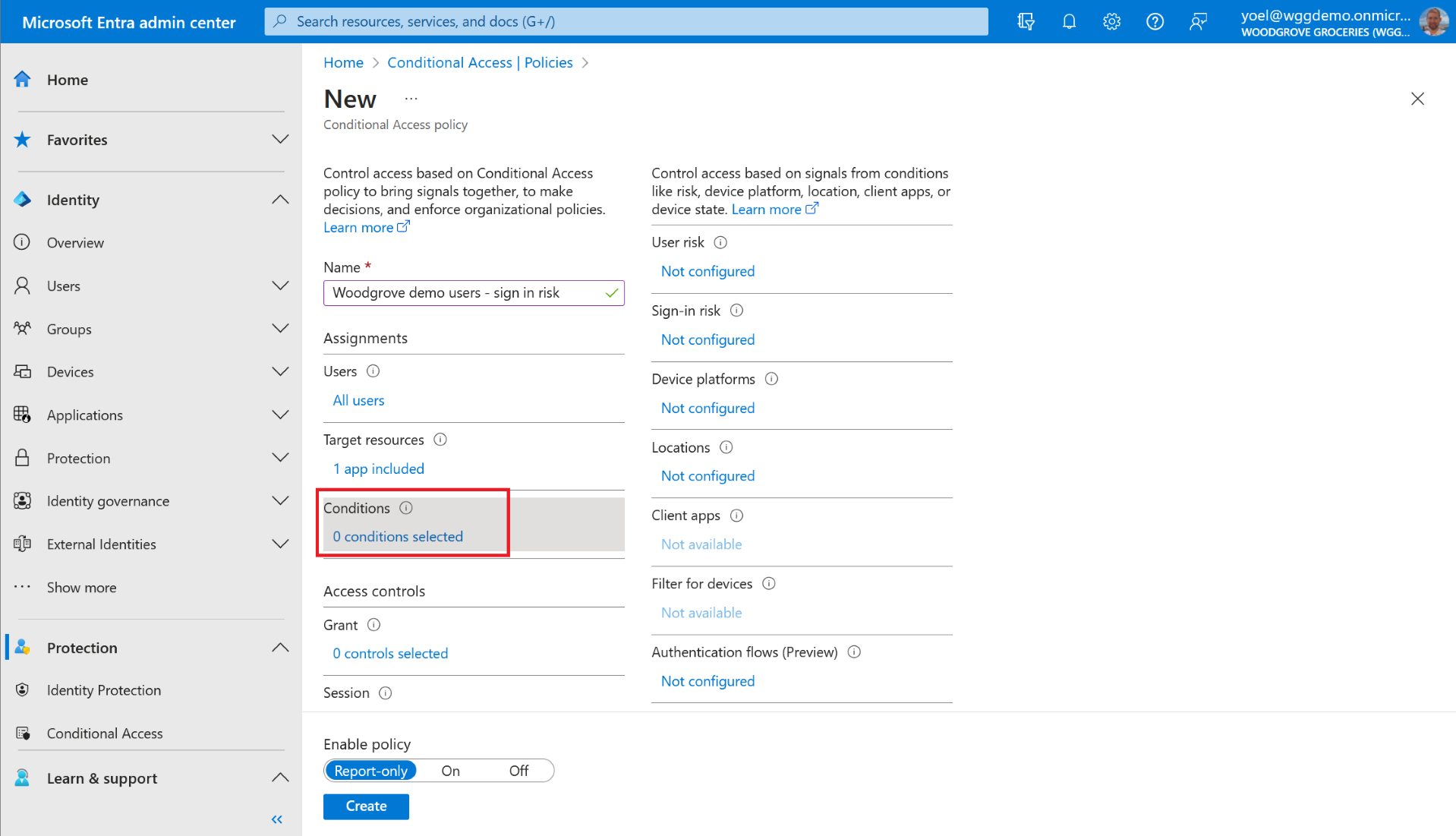
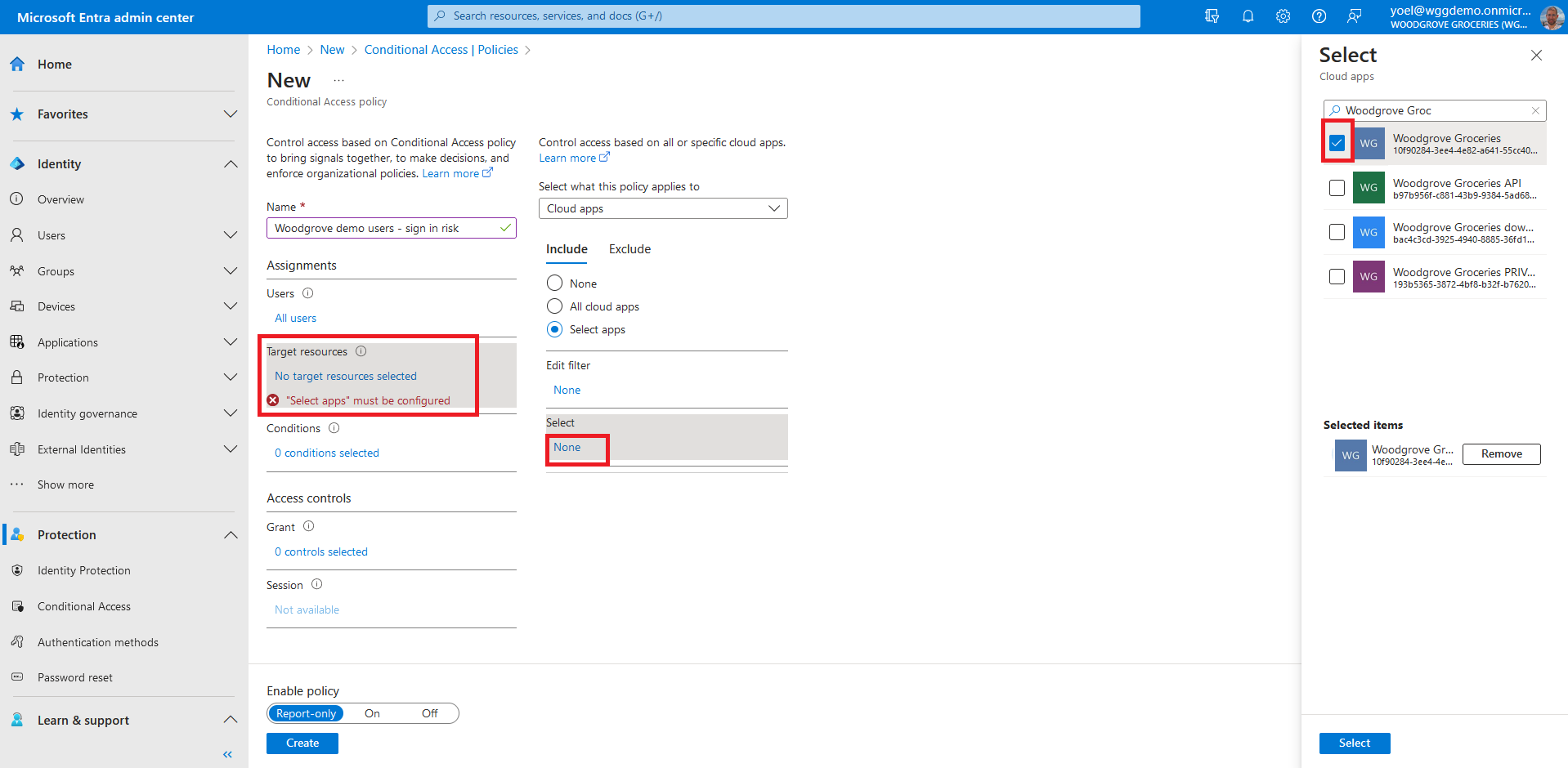
Under assignments, select Target resources. Then, On the Include tab, choose the Select apps option and click on the Select button. Find your app, select it, and then choose Select.
Create conditional access policy
The following example creates a conditional access policy. This policy targets all sign-ins for all users (excludes tenant global administrator). In the JSON below, replace the {web-or-mobile-app-ID} with your web or mobile application (App ID, not object ID). Note, you can add more applications.
POST https://graph.microsoft.com/v1.0/identity/conditionalAccess/policies
{
"templateId": null,
"displayName": "Woodgrove demo - sign in risk",
"state": "enabled",
"sessionControls": null,
"conditions": {
"userRiskLevels": [],
"signInRiskLevels": [
"high",
"medium"
],
"clientAppTypes": [
"all"
],
"platforms": null,
"locations": null,
"times": null,
"deviceStates": null,
"devices": null,
"clientApplications": null,
"applications": {
"includeApplications": [
"{web-or-mobile-app-ID}"
],
"excludeApplications": [],
"includeUserActions": [],
"includeAuthenticationContextClassReferences": [],
"applicationFilter": null
},
"users": {
"includeUsers": [
"All"
],
"excludeUsers": [],
"includeGroups": [],
"excludeGroups": [],
"includeRoles": [],
"excludeRoles": [],
"includeGuestsOrExternalUsers": null,
"excludeGuestsOrExternalUsers": null
}
},
"grantControls": {
"operator": "OR",
"builtInControls": [
"mfa"
],
"customAuthenticationFactors": [],
"termsOfUse": [],
"authenticationStrength": null
}
}