Enable self-service password reset
Self-service password reset (SSPR) in Microsoft Entra ID gives customers the ability to change or reset their password, with no administrator or help desk involvement. If a customer's account is locked or they forget their password, they can follow prompts to unblock themselves and get back to work. This demo shows how to enable (SSPR) in Microsoft Entra External ID.
Prerequisites
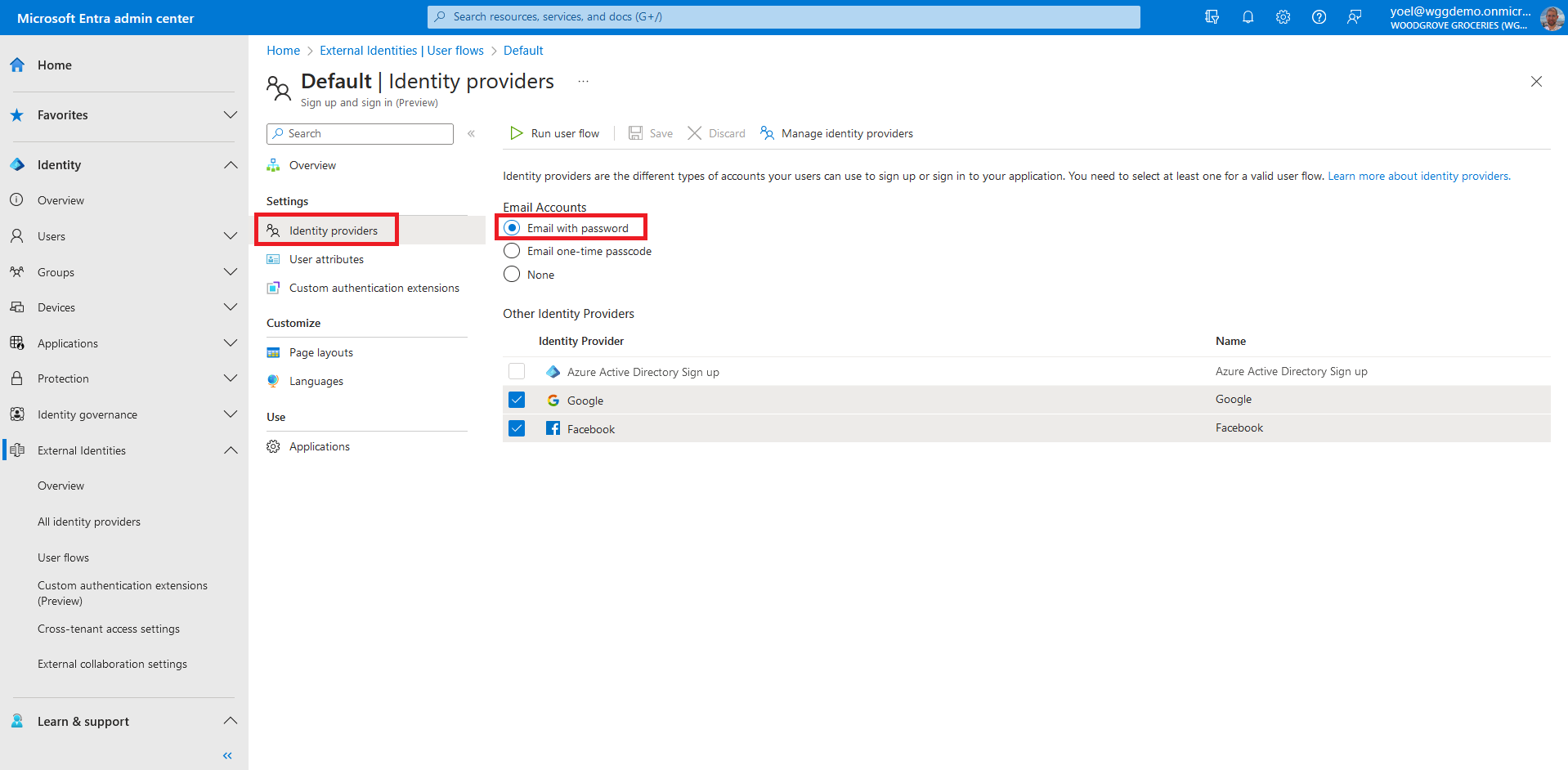
Before you start make sure you have configured the following:To enable self-service password reset, first make sure that the sign-up user flow registers Email with password as an authentication method. Sign in to the Microsoft Entra admin center and browse to External Identities > User flows. Then, select the user flow that you want to check.
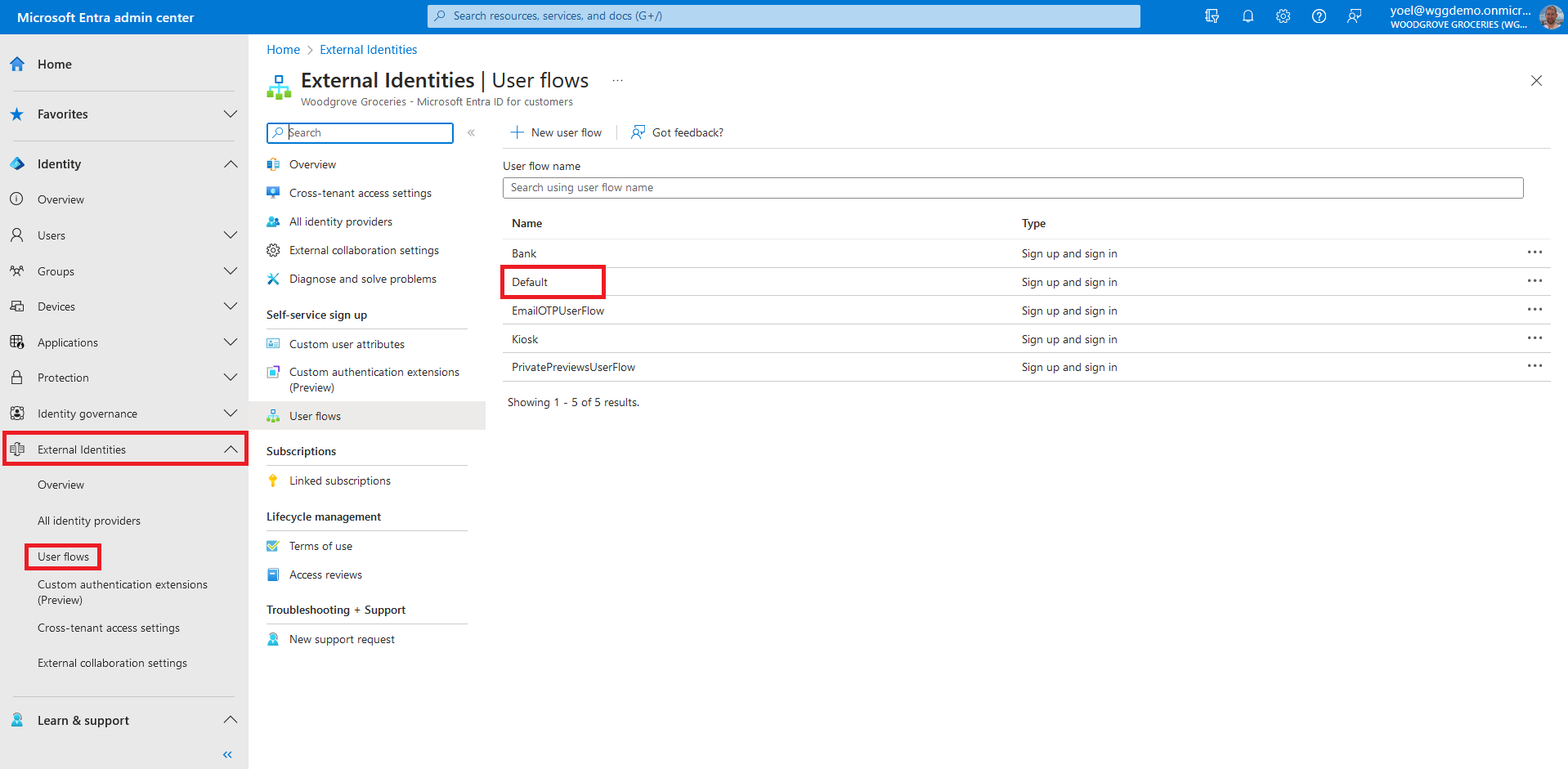
In the user flow, select Identity providers. Then, under Email Accounts, make sure that the sign-up user flow registers Email with password as an authentication method.
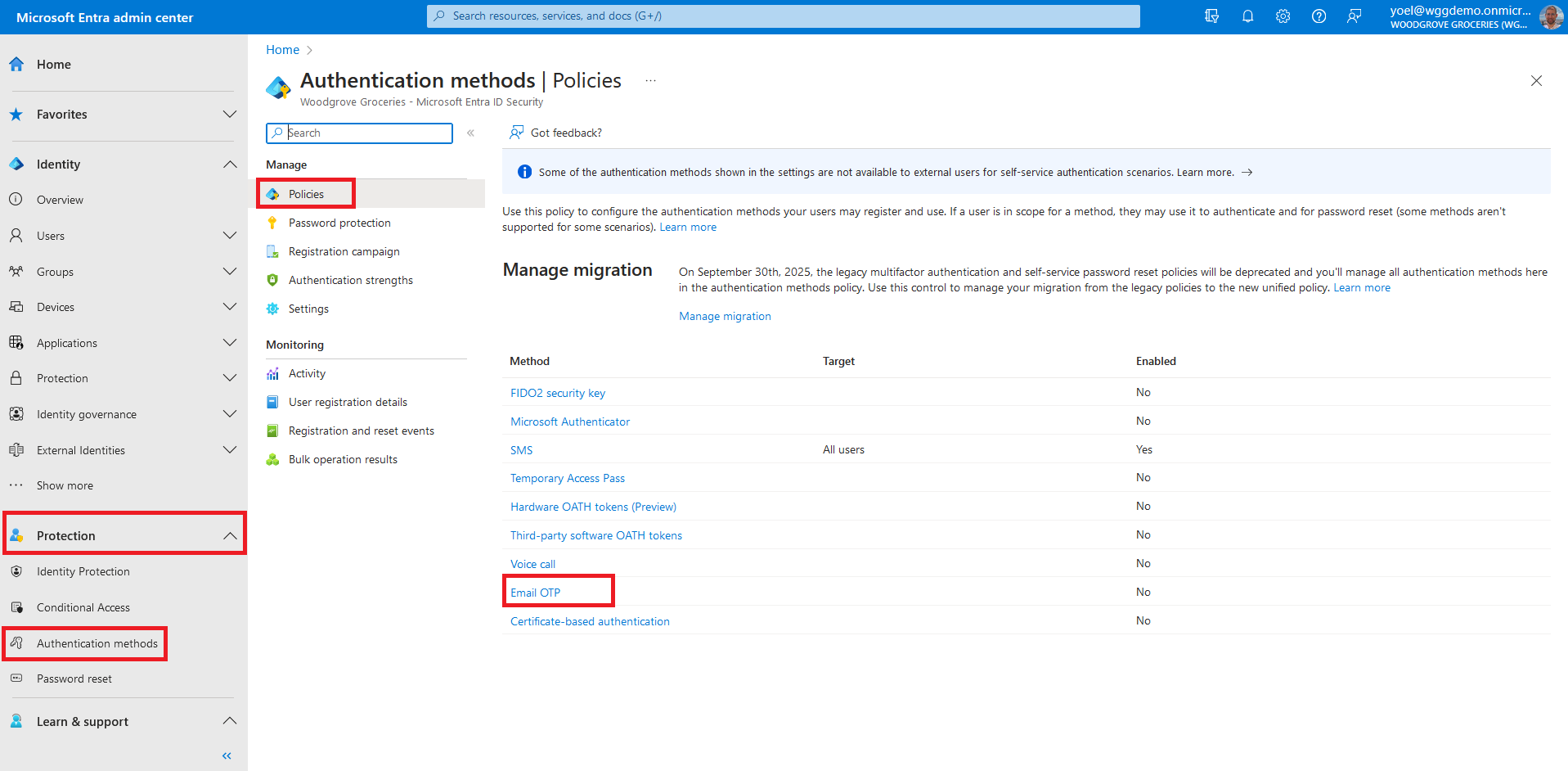
The self-service password uses the email one-time passcode (Email OTP) authentication. In the next steps you enable Email OTP authentication method for all users in your tenant. Browse to Identity > Protection > Authentication methods. Under Policies > Method, select Email OTP.
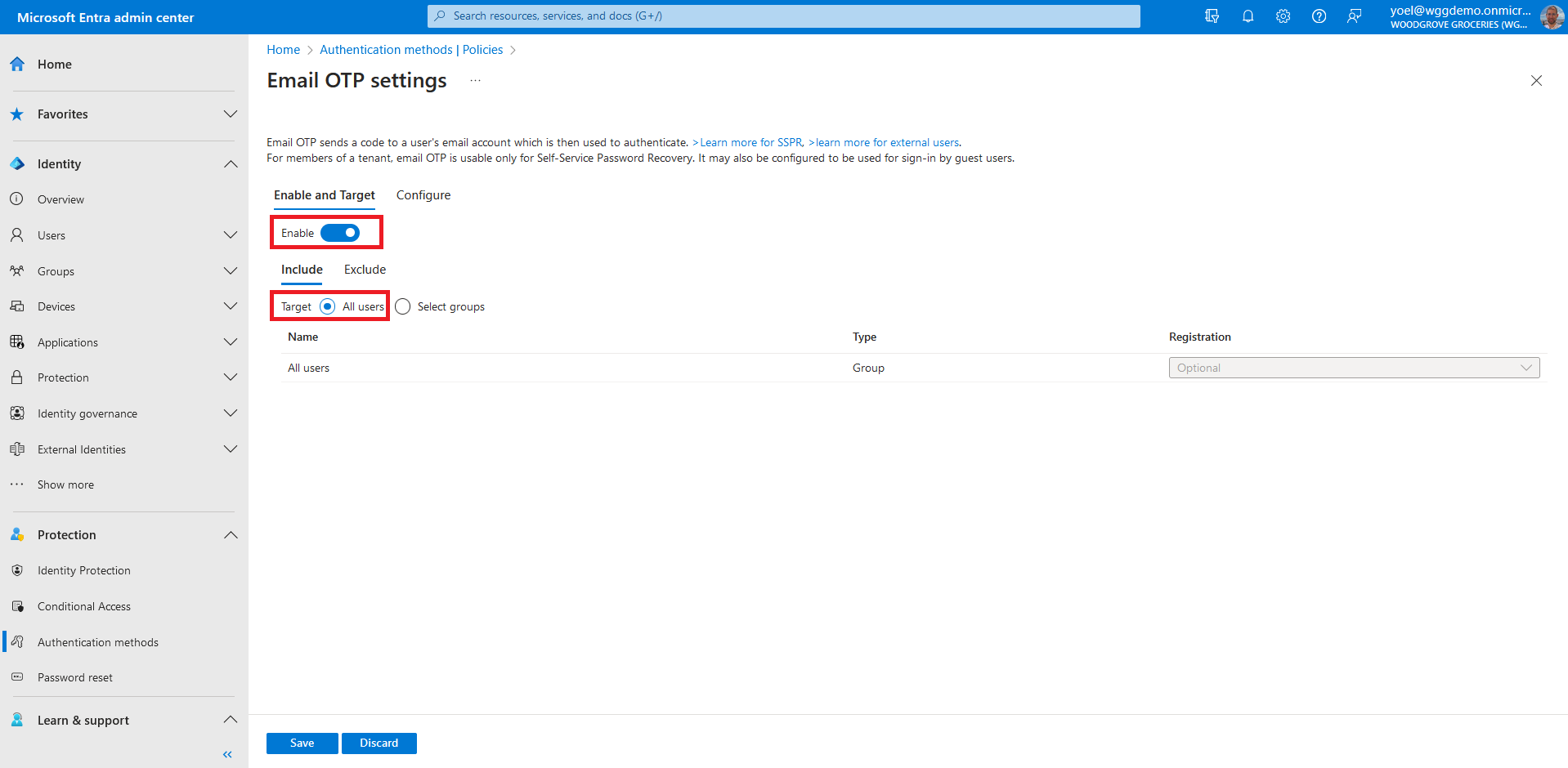
Under Enable and Target enable Email OTP and under Include, select All users. Then, select Save to enable the email OTP authentication method.
Well done!
You made sure your user flow supports Email with password sign-in. Then you enabled the email OTP authentication method for all users in the tenant. To check the user experience, sign-in to your application and select the Forgot password? link.
If the Forgot password? link doesn't appear, move to the next step.
Enable the password reset link
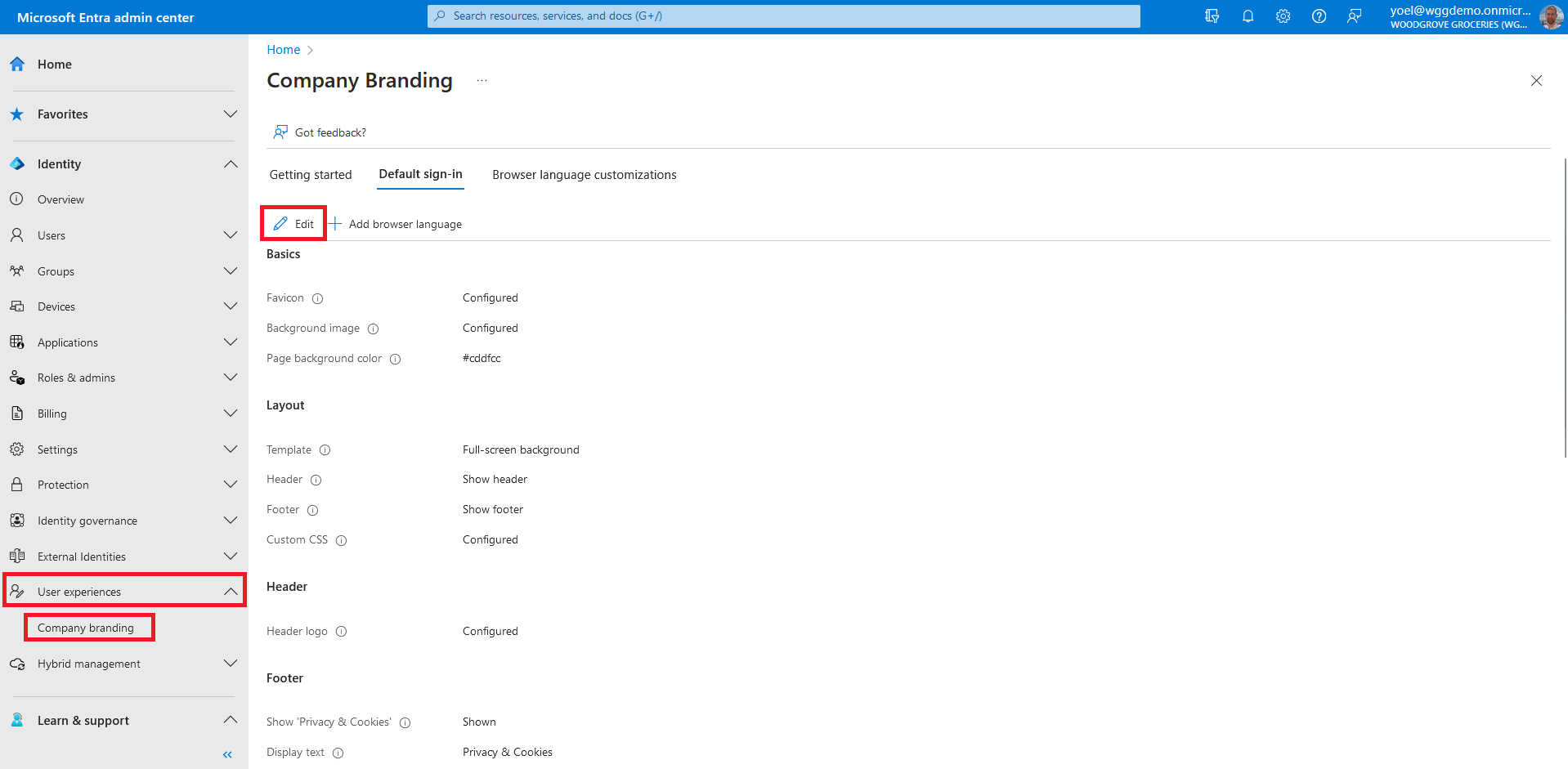
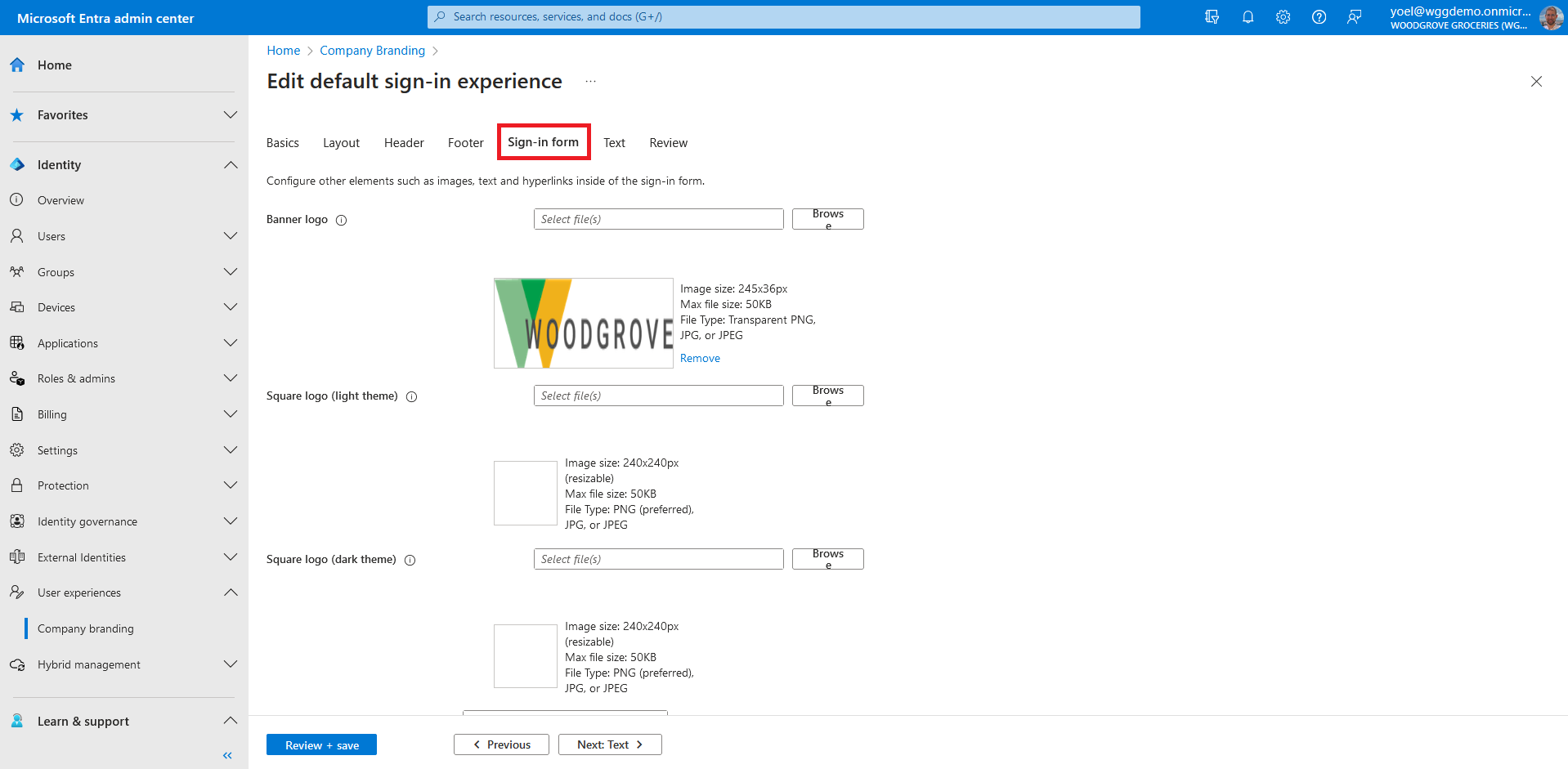
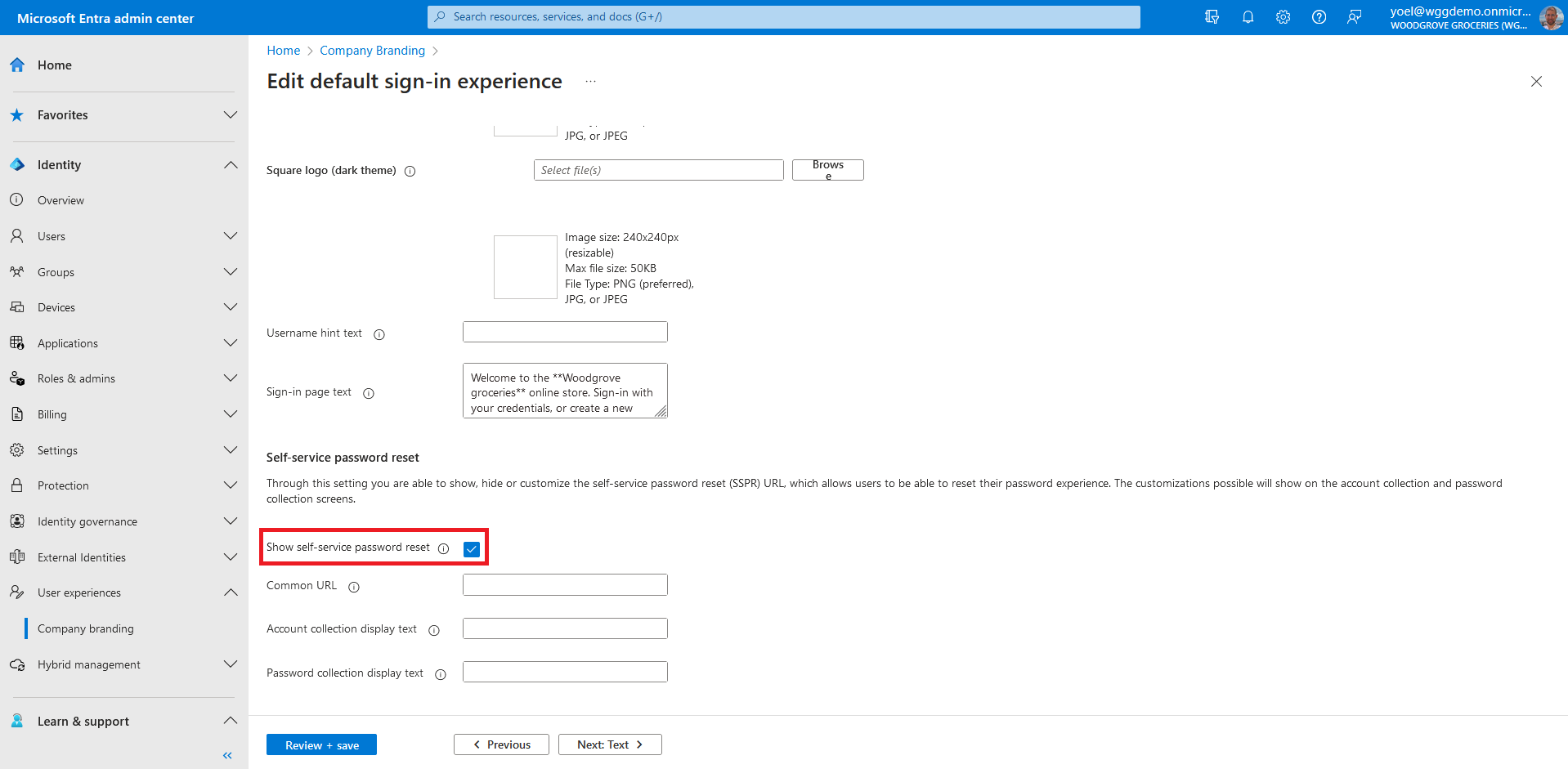
If the Forgot password? link doesn't appear, you should enable the password reset link. Browse to Identity > User experience > Company Branding If you can't find it in the menu, select Show more....
Enable Email OTP authentication method
The following Graph enables email OTP authentication method for all users in your tenant.
PATCH https://graph.microsoft.com/v1.0/policies/authenticationMethodsPolicy/authenticationMethodConfigurations/email
{
"state": "enabled",
"allowExternalIdToUseEmailOtp": "default",
"excludeTargets": [],
"includeTargets": [
{
"targetType": "group",
"id": "all_users",
"isRegistrationRequired": false
}
]
}