Sign-in with social or enterprise identity providers (federation)
By setting up federation with social identity providers, you can allow users to sign in to your applications with their own social account, such as Facebook or Google. This demo shows how to add Facebook as one of your application's sign-in options. On the sign-in page, users can sign-in to Microsoft Entra ID with Facebook. The steps in this demo applies also to other identity providers, such as Google.
Prerequisites
Before you start make sure you have configured the following:To add Facebook as an identity provider, you first need to create an application in Facebook identity provider. Then, configure the federation in Microsoft Entra External ID. After you created an application in Facebook, sign in to the Microsoft Entra admin center and browse to External Identities > External Identities > All identity providers. Then, select + Facebook.
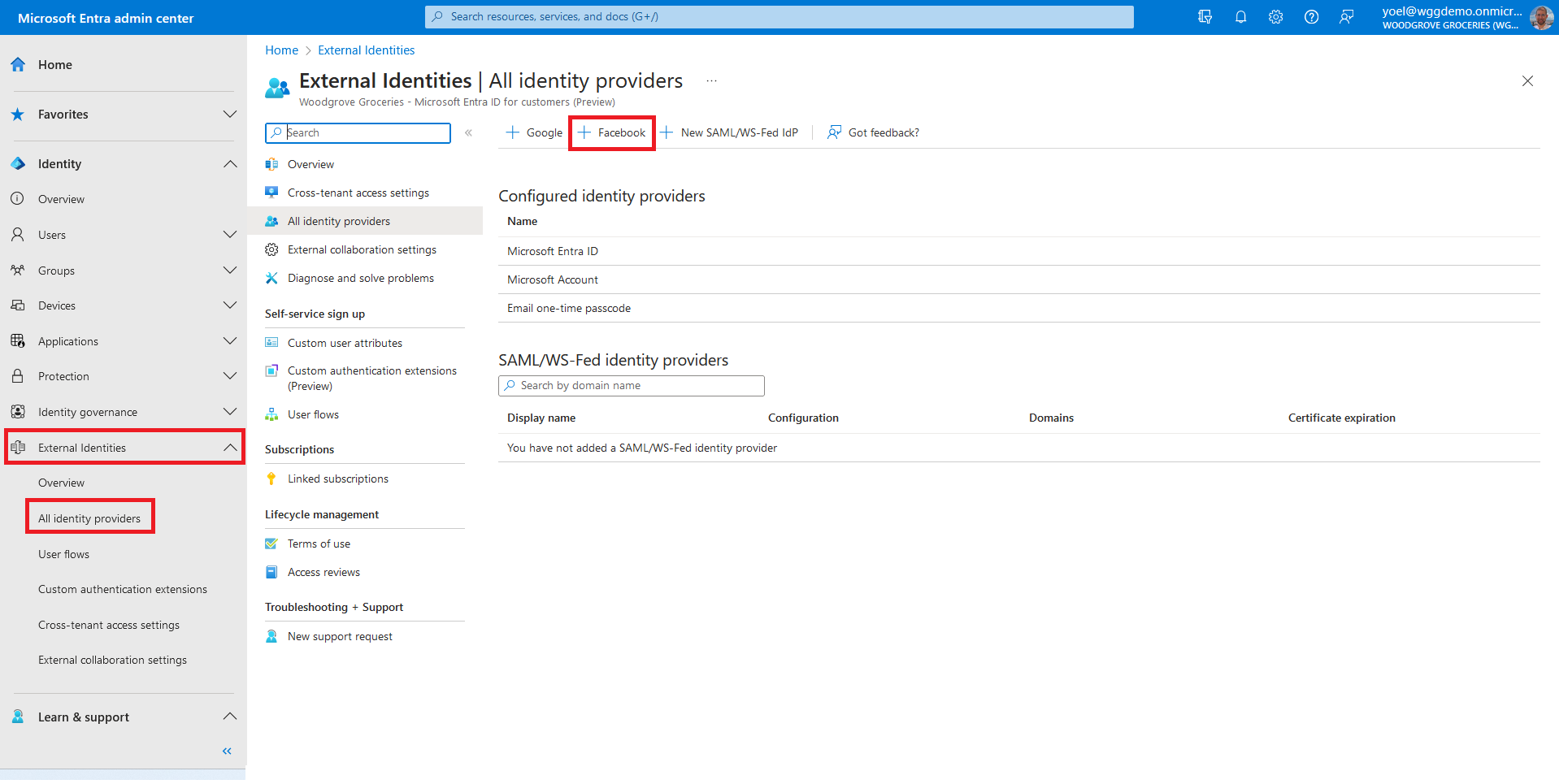
For the Client ID, enter the client ID of the Facebook application that you created earlier. For the Client secret, enter the client secret that you recorded. Then, select Save.
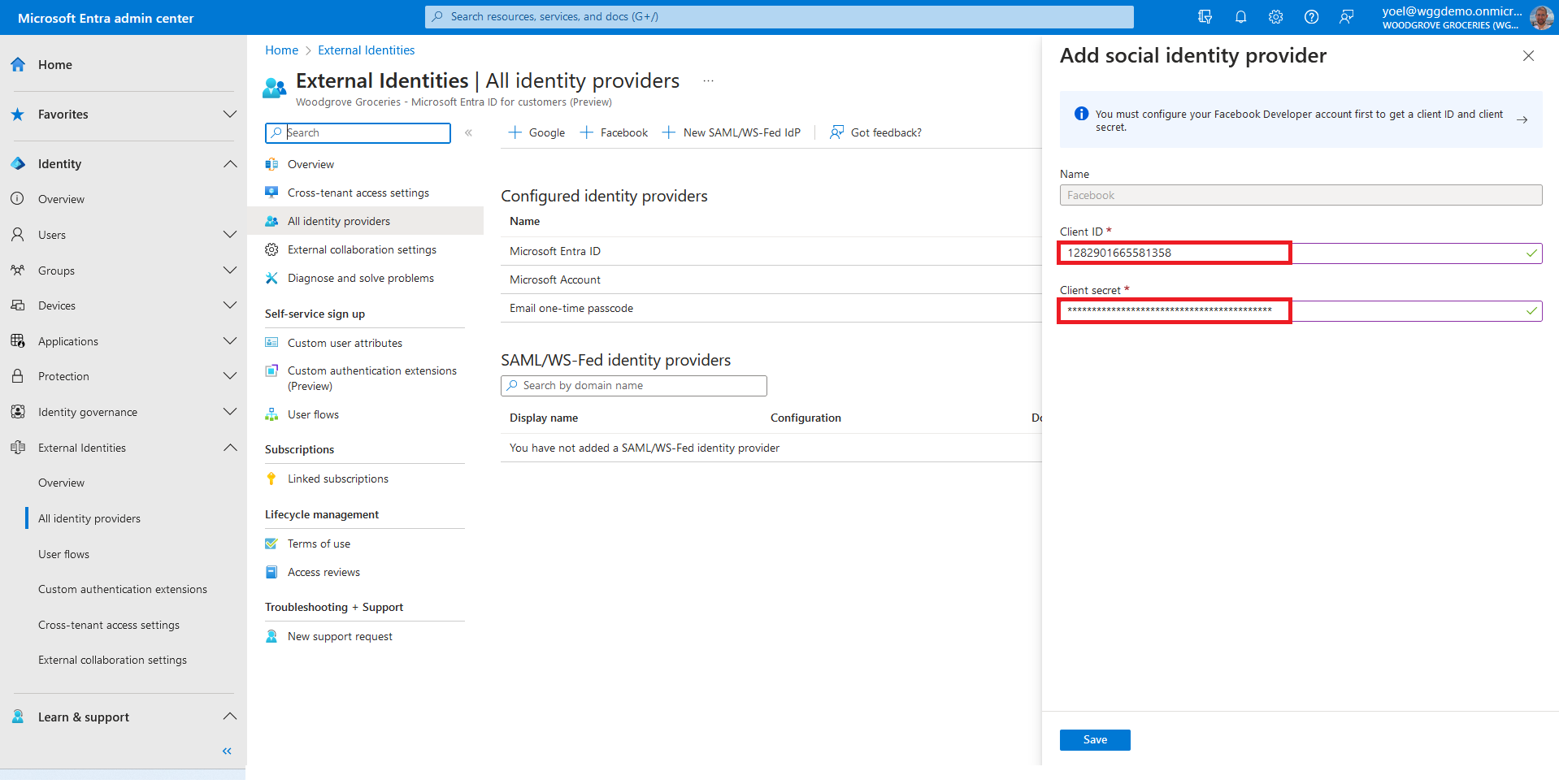
At this point, the Facebook identity provider has been set up in your Microsoft Entra ID, but it's not yet available in any of the sign-in pages. You need to add the Facebook identity provider to a user flow. In your Entra external ID tenant, browse to Identity > External Identities > User flows. Then, Select the user flow where you want to add the Facebook identity provider.
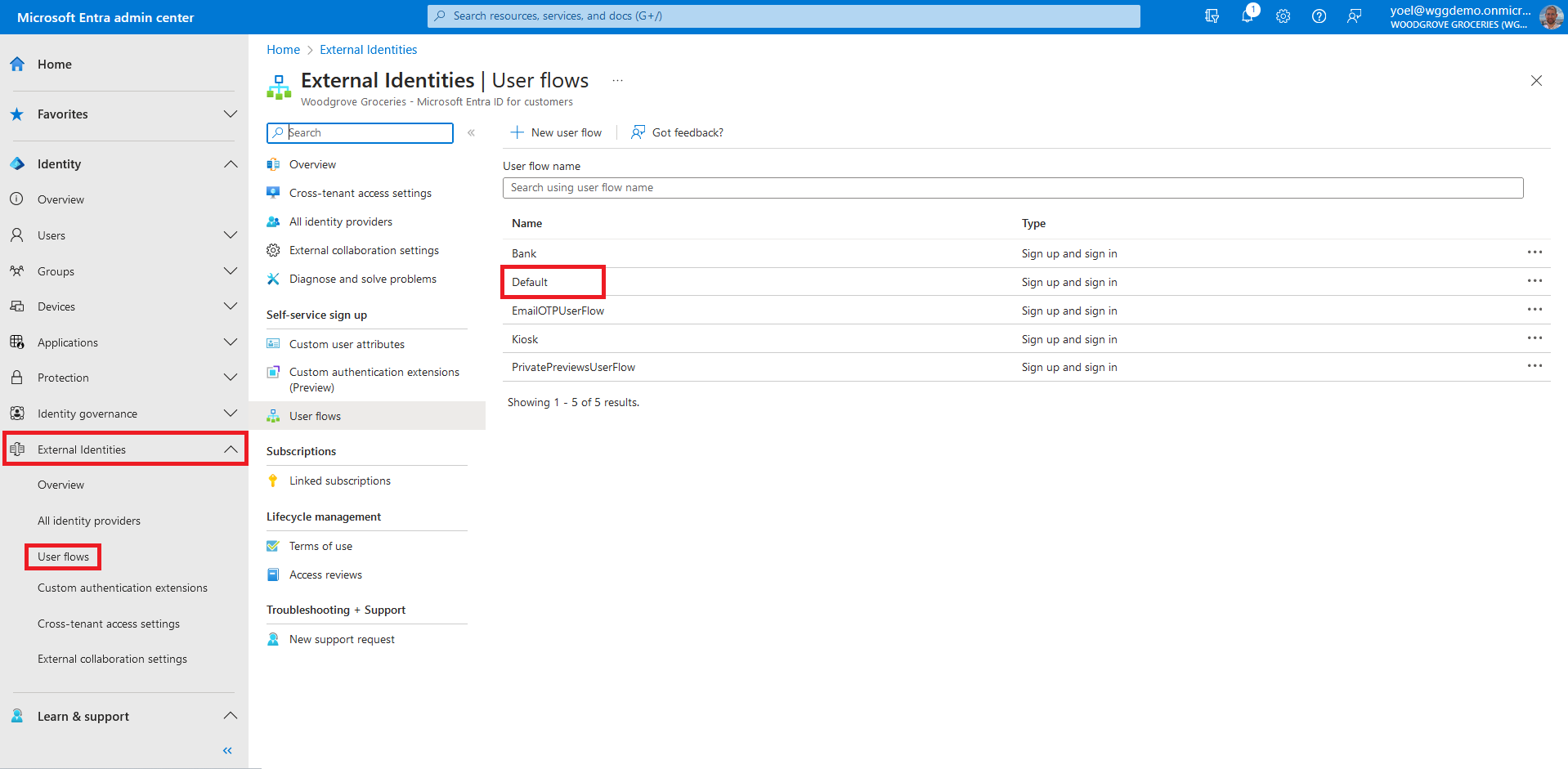
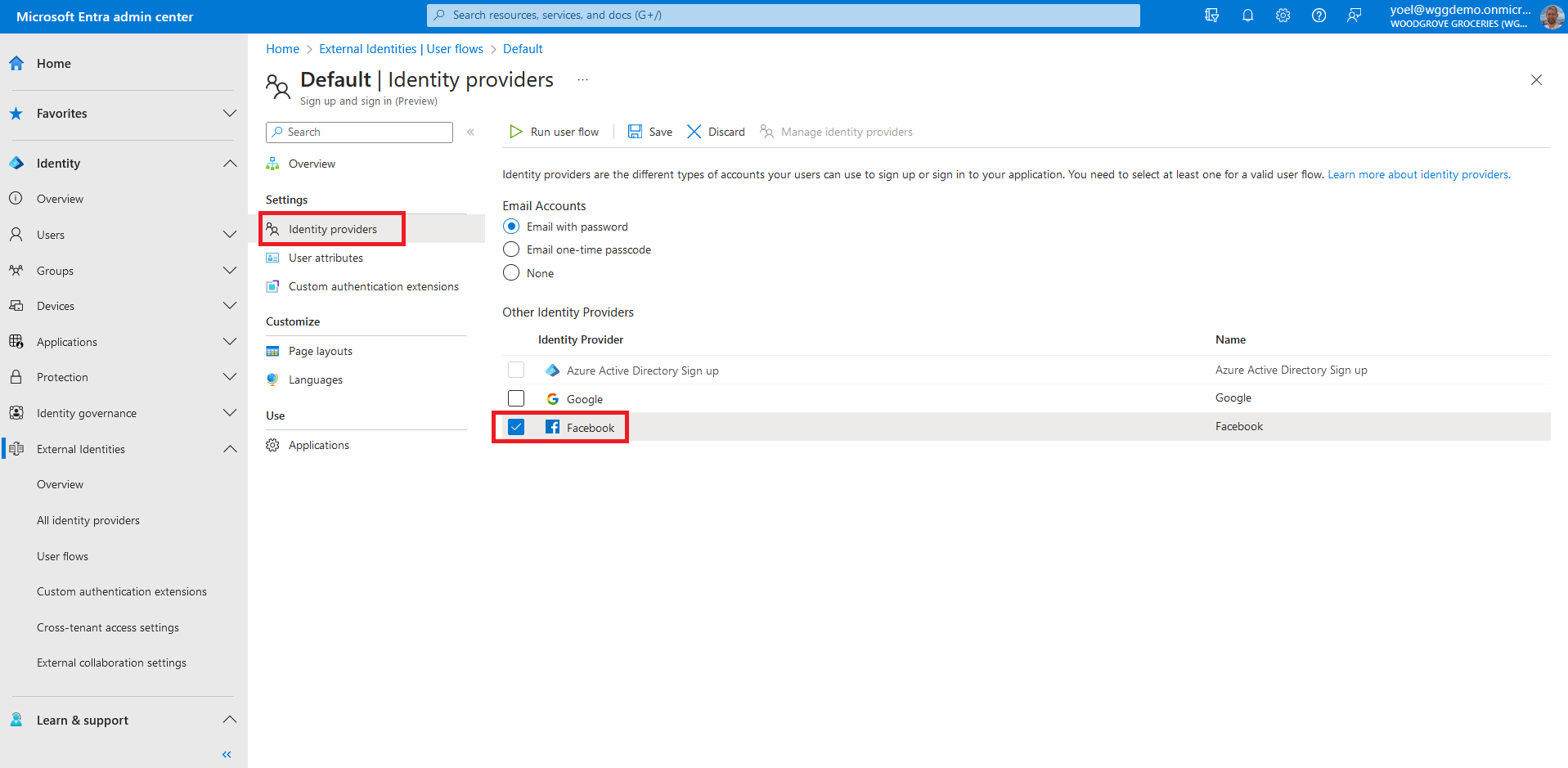
Under Settings, select Identity providers. Under Other Identity Providers, select Facebook. At the top of the pane, select Save.
Well done!
You successfully added the Facebook identity provider to your tenant. Then you enabled the sign-in with Facebook in your user flow. To check the user experience, sign-in to your application and select the Facebook option.
Dependencies
- User flow
1. Register Facebook
To add Facebook as an identity provider, you first need to create an application in Facebook identity provider. Then, register the identity provider in your Microsoft Entra external ID tenant with the following Microsoft Graph. Replace the {Facebook app ID} with the App ID of the Facebook application that you created earlier. Replace the {Facebook app secret} with the App Secret that you recorded.
POST https://graph.microsoft.com/beta/identity/identityProviders
{
"@odata.type": "#microsoft.graph.socialIdentityProvider",
"displayName": "Facebook",
"identityProviderType": "Facebook",
"clientId": "{Facebook app ID}",
"clientSecret": "{Facebook app secret}"
}
1.1 Copy the Facebook provider ID
From the response, copy the value of the Facebook identity provider id. For example:
{
"@odata.context": "https://graph.microsoft.com/beta/$metadata#identity/identityProviders/$entity",
"@odata.type": "#microsoft.graph.socialIdentityProvider",
"id": "11111111-0000-0000-0000-000000000000",
"identityProviderType": "Facebook",
"displayName": "Facebook",
"supportedTenantTypes": "externalId",
}
1.2 Add Facebook identity provider to a user flow
After you register the Facebook identity provider to your Microsoft Entra external ID tenant, you can add it to your user flow. In the following Microsoft Graph, replace:
- {user-flow-ID} with your user flow ID
- {identity-provider-ID} with the ID of the identity provider you copied earlier.
POST https://graph.microsoft.com/beta/identity/authenticationEventsFlows/{user-flow-ID}/microsoft.graph.externalUsersSelfServiceSignUpEventsFlow/onAuthenticationMethodLoadStart/microsoft.graph.onAuthenticationMethodLoadStartExternalUsersSelfServiceSignUp/identityProviders/$ref
{
"@odata.id": "https://graph.microsoft.com/beta/identity/identityProviders/{identity-provider-ID}"
}
2. Register Google
To add Google as an identity provider, you first need to create an application in Google identity provider. Then, register the identity provider in your Microsoft Entra external ID tenant. Replace the {Google app ID} with the App ID of the Google application that you created earlier. Replace the {Google app secret} with the App Secret that you recorded.
POST https://graph.microsoft.com/beta/identity/identityProviders
{
"@odata.type": "#microsoft.graph.socialIdentityProvider",
"displayName": "Google",
"identityProviderType": "Google",
"clientId": "{Google app ID}",
"clientSecret": "{Google app secret}"
}
1.1 Copy the Google provider ID
From the response, copy the value of the Google identity provider id. For example:
{
"@odata.context": "https://graph.microsoft.com/beta/$metadata#identity/identityProviders/$entity",
"@odata.type": "#microsoft.graph.socialIdentityProvider",
"id": "11111111-0000-0000-0000-000000000000",
"identityProviderType": "Google",
"displayName": "Google",
"supportedTenantTypes": "externalId",
}
2.1 Add Google identity provider to a user flow
After you register the Google identity provider to your Microsoft Entra external ID tenant, you can add it to your user flow. In the following Microsoft Graph, replace:
- {user-flow-ID} with your user flow ID
- {identity-provider-ID} with the ID of the identity provider you copied earlier.
POST https://graph.microsoft.com/beta/identity/authenticationEventsFlows/{user-flow-ID}/microsoft.graph.externalUsersSelfServiceSignUpEventsFlow/onAuthenticationMethodLoadStart/microsoft.graph.onAuthenticationMethodLoadStartExternalUsersSelfServiceSignUp/identityProviders/$ref
{
"@odata.id": "https://graph.microsoft.com/beta/identity/identityProviders/{identity-provider-ID}"
}