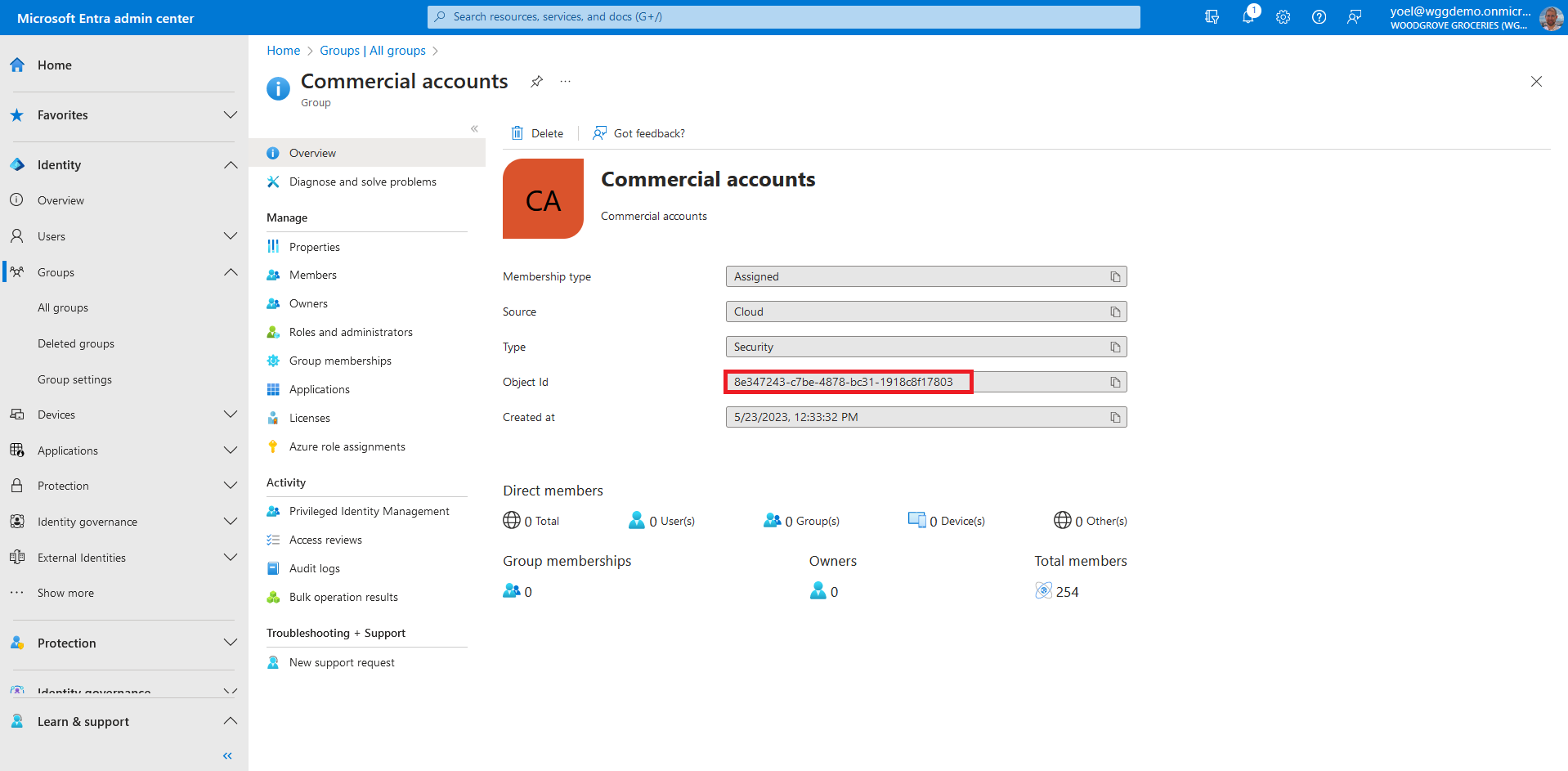
Group-based access control
Group-based access control is a popular mechanism to enforce authorization in applications. It helps you manage who has access to your application and what they can do in the application. You can also alter the UI based on the user's membership. In this demo, users add themselves to the Commercial Accounts security group and will get discounts for some of the products.
Prerequisites
Before you start make sure you have configured the following:Start by creating a security group. Sign-in to the Microsoft Entra admin center and browse to Identity > Groups > All groups. Then, select New group.
Under Group type dropdown, select Security. Enter a Group name, such as Commercial accounts. Enter Group description, such as Woodgrove commercial accounts. You can also add Memebers now, or do it later. Finally, select Create.
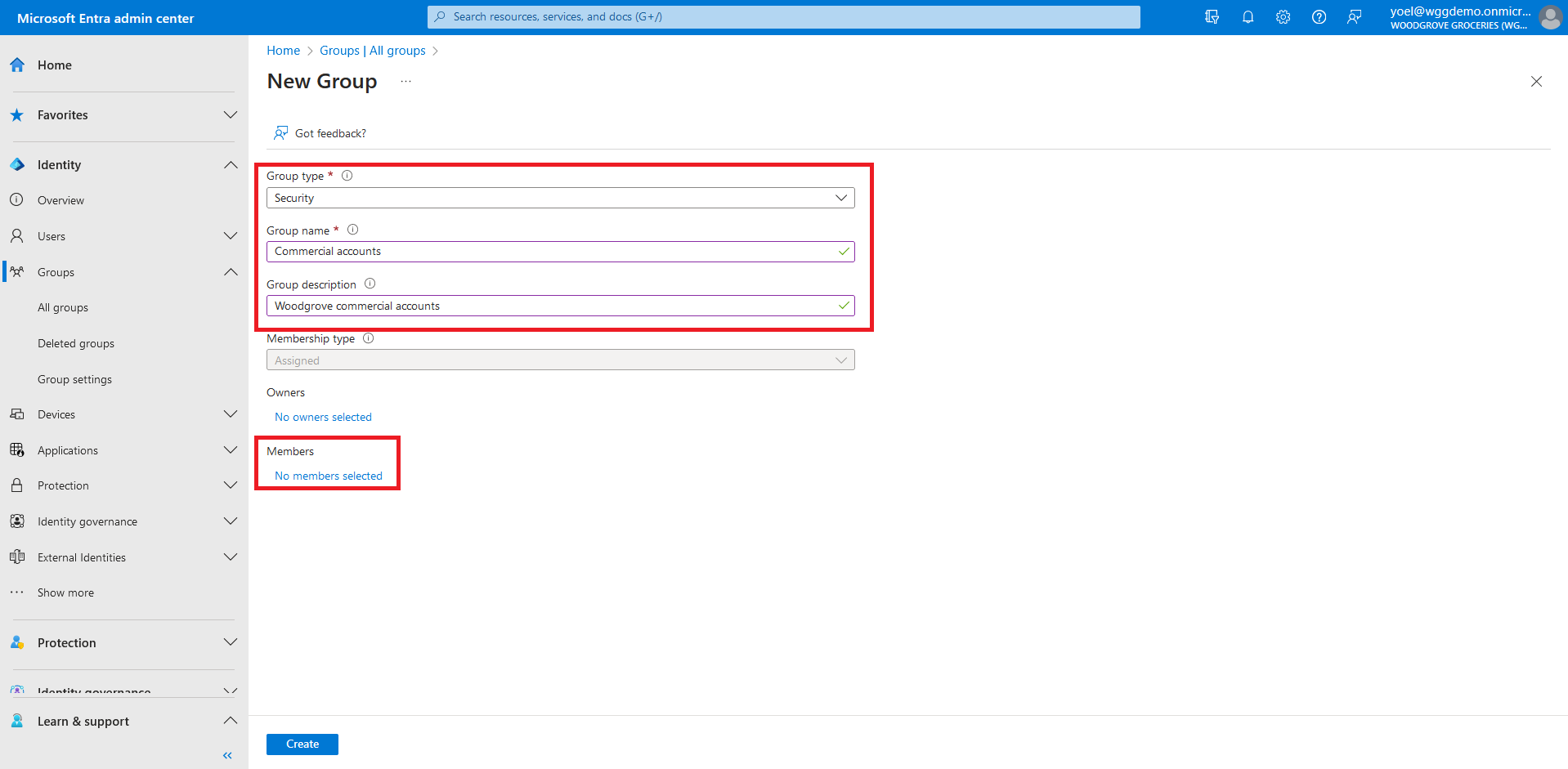
The new security group appears in the All groups list. If you don't see it immediately, refresh the page and select the security group.
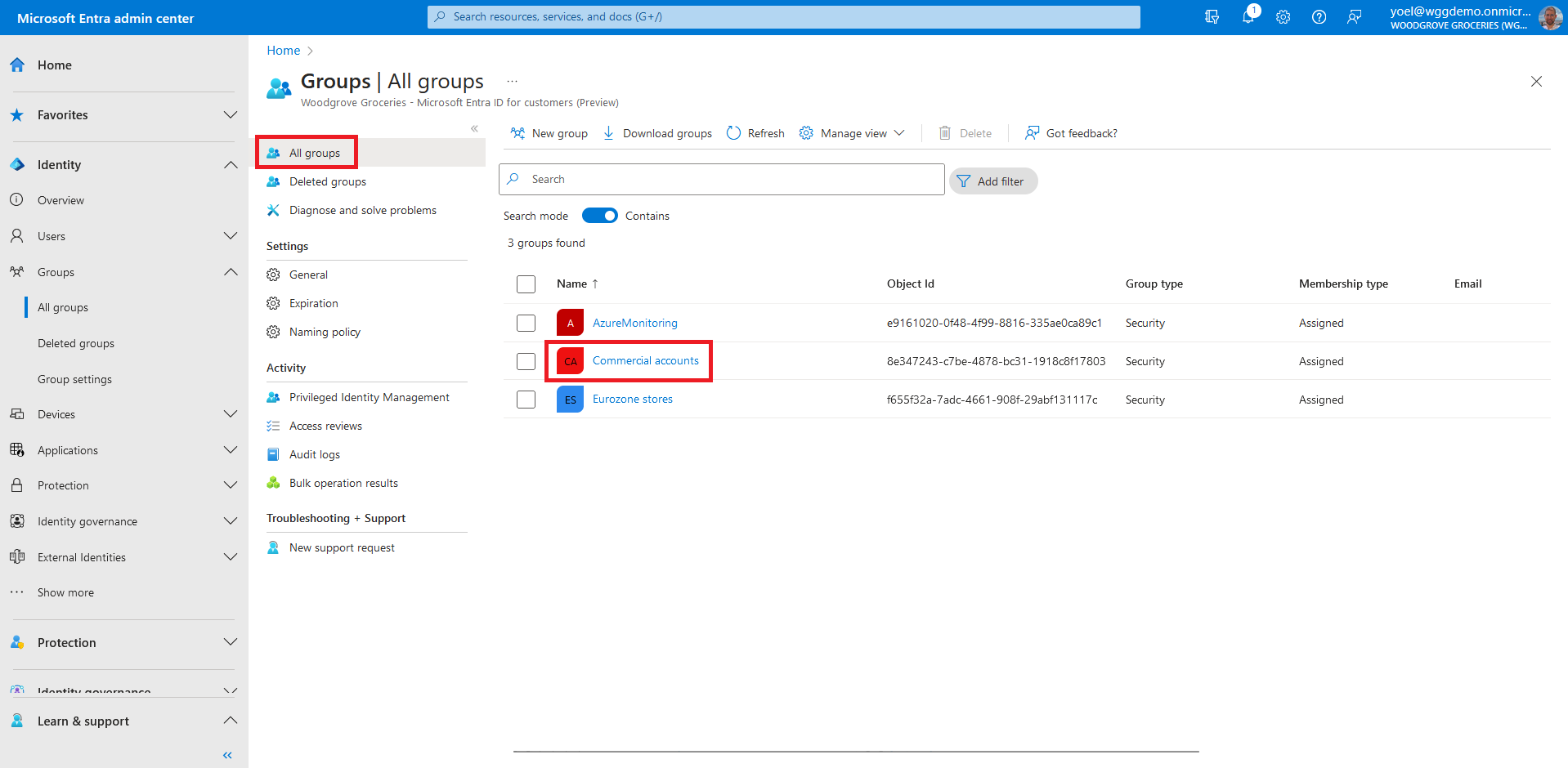
Once you've created the security group, you can add users. You can also do it programmatically using Microsoft Graph. To add users to a security group, select Members. Then select Add members.
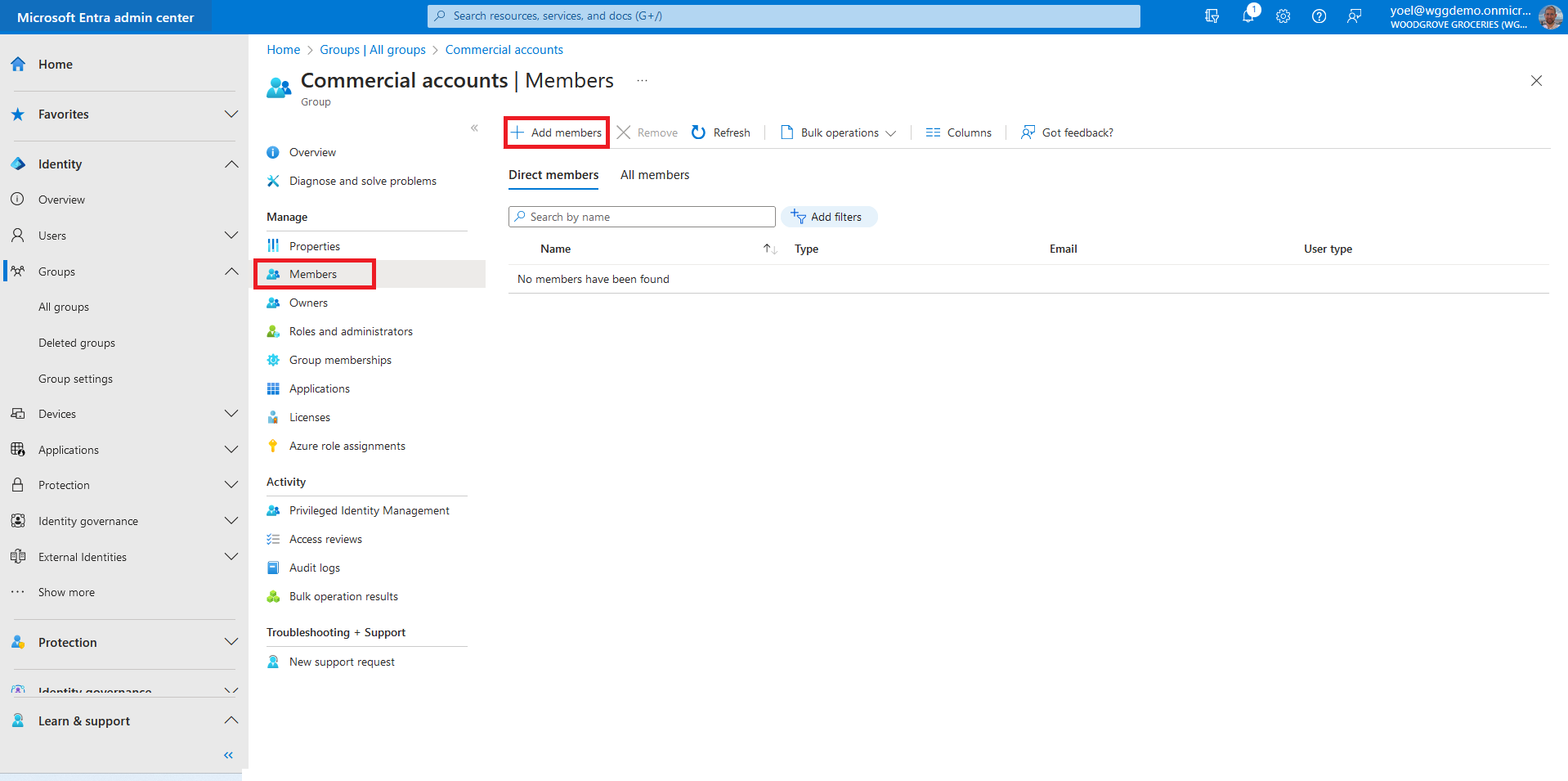
Scroll through the list or enter a name in the search box. You can choose multiple names. When you're ready, choose Select.
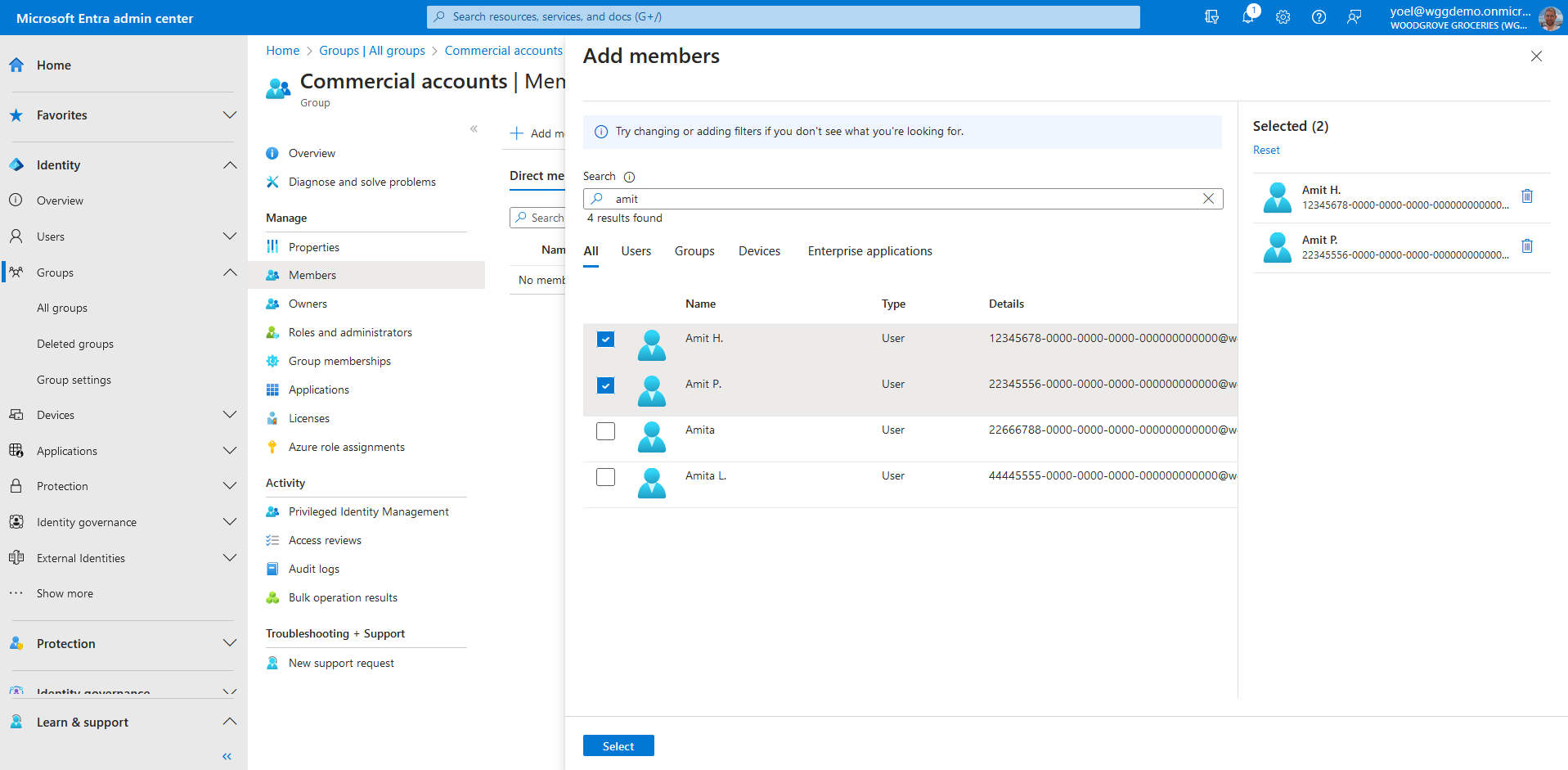
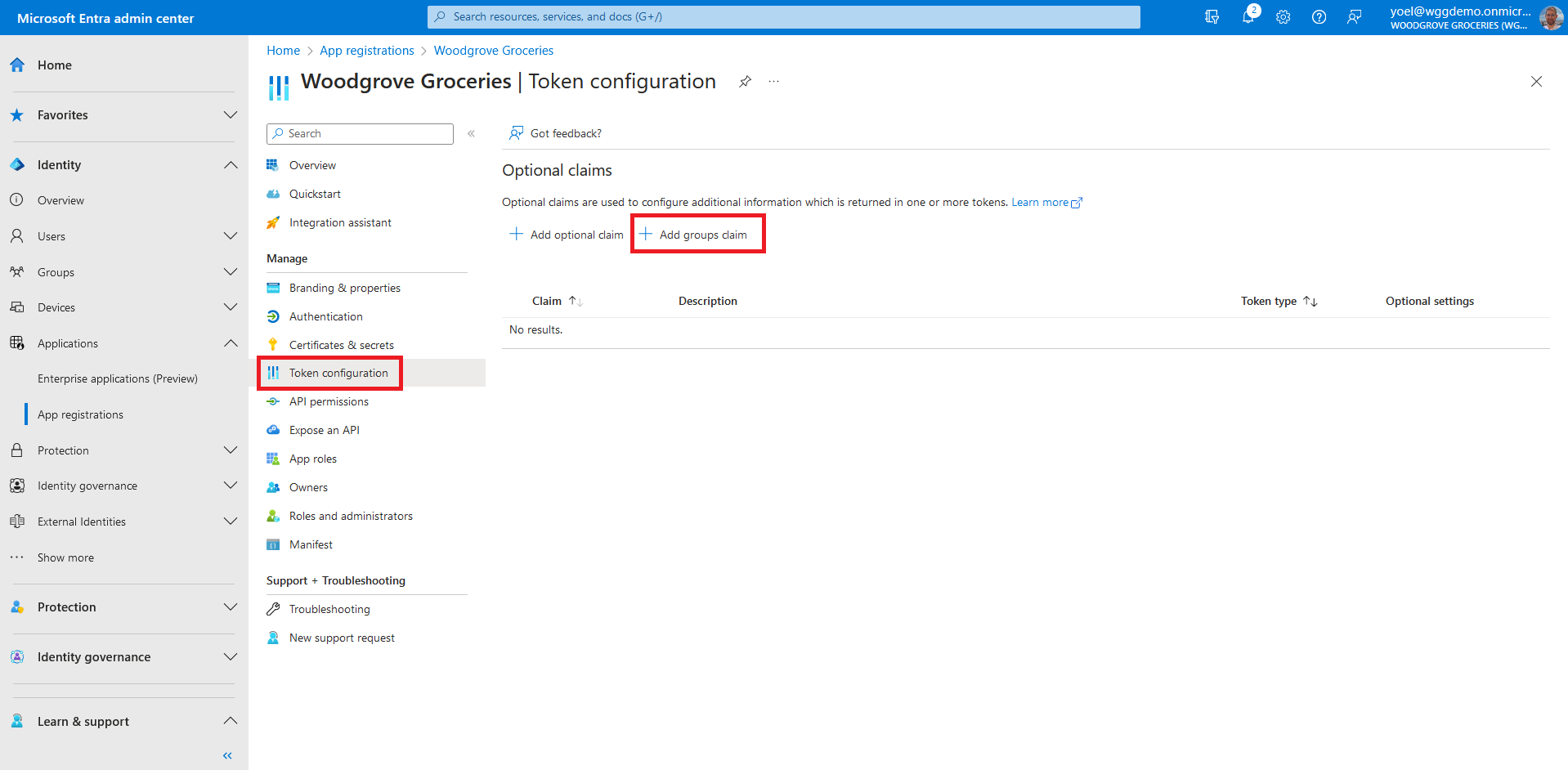
Now that you have a security group and also added users, it's time to configure the app to include the groups claims into security tokens. To emit the group membership claims in security tokens, browse to Identity > Applications > App registrations. Then, select the application in which you want to add the groups claim.
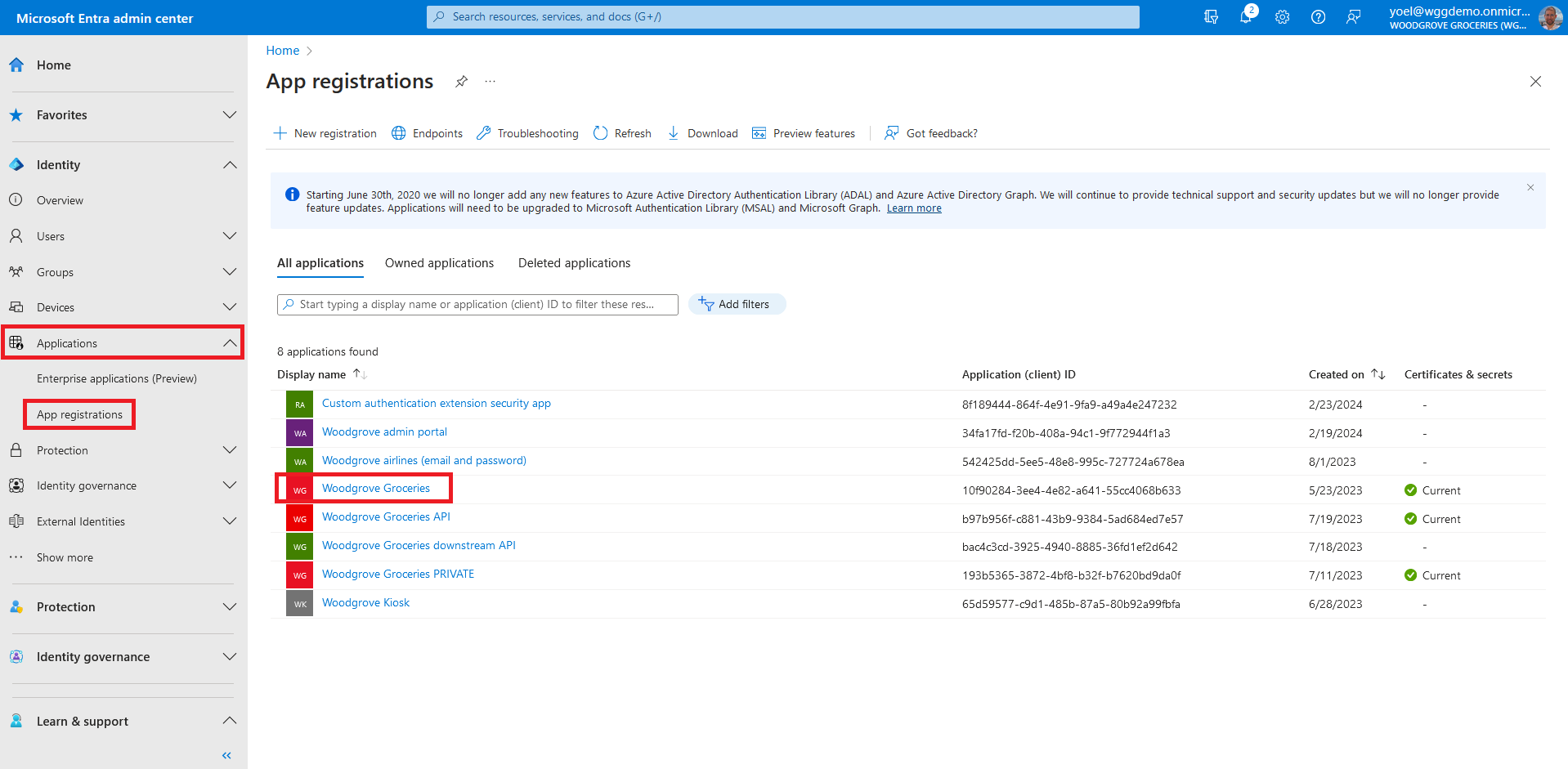
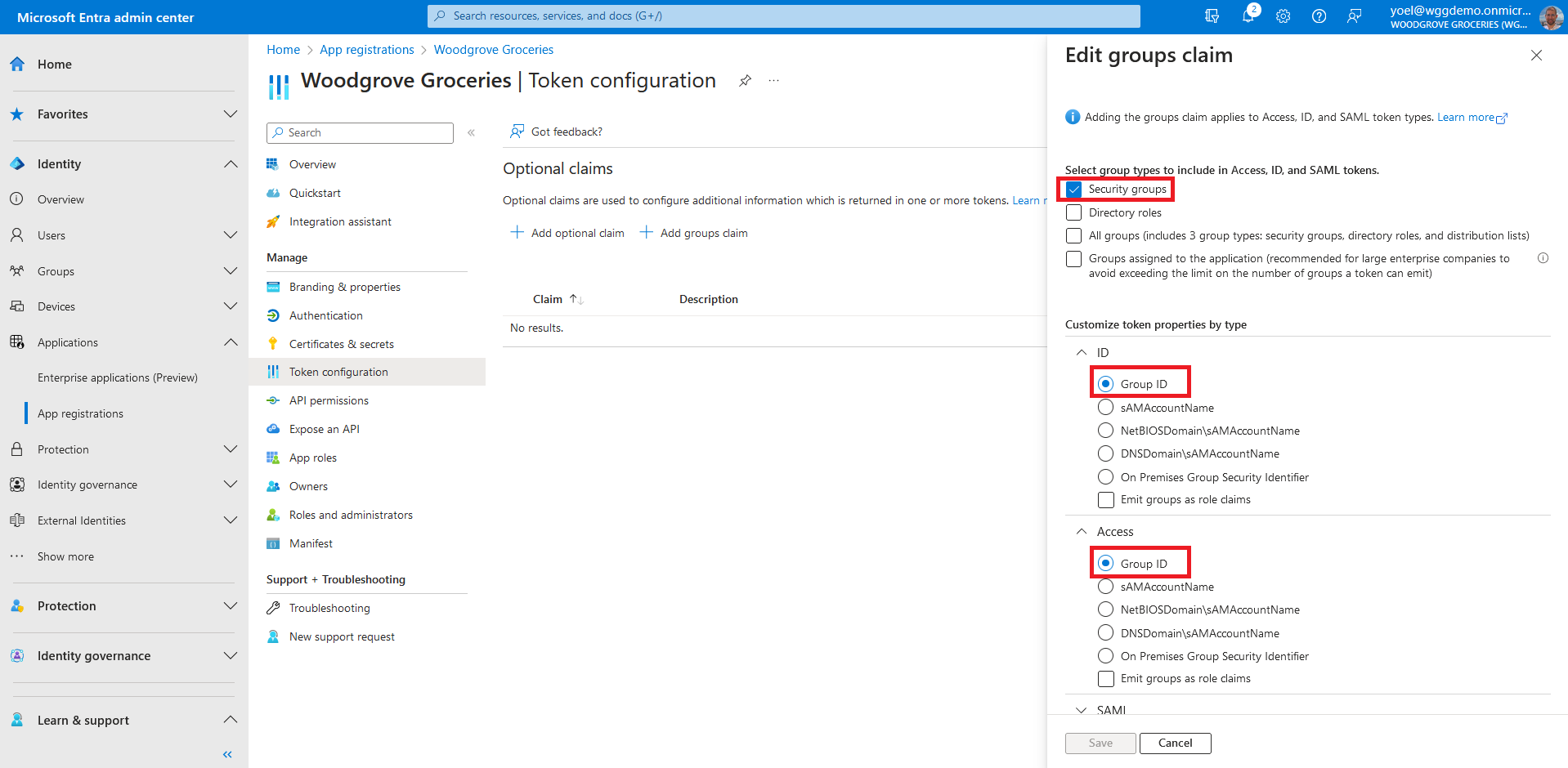
Select Security group types to include in the security tokens. For the Customize token properties by type, select Group ID for all of the tokens ID, Access and SAML (for SAML app). Select Add to add the groups claim.
Well done!
You created a security group, added users and then include the groups claim in the security tokens. Now if the sign-in user is a member of any socurity group, the groups claim will be included in security tokens.
Next you will have to configuration your application to check the value of the groups claim.
For example you can check the claim value in your code:
// Check whether the account is commercial
string commercialAccountsSecurityGroup = Configuration.GetSection("AppRoles:CommercialAccountsSecurityGroup").Value;
IsCommercialAccount = User.Claims.Any(c => c.Type == "groups" && c.Value == commercialAccountsSecurityGroup);
Create a security group
Start by creating a security group. After the group is creaetd, take a note of the security group object id. You will use the ID to configure your application.
POST https://graph.microsoft.com/v1.0/groups
{
"description": "Commercial accounts",
"displayName": "Woodgrove commercial accounts",
"mailNickname": "CommercialAccounts",
"securityEnabled": true,
"mailEnabled": false
}
Add a member to the security group
Once you've created the security group, you can add users. In the following Graph, replace the {group-id} with the group ID you created. And replace the {user-id-*} with the user object ID you want to add.
POST https://graph.microsoft.com/v1.0/groups/{group-id}/members/$ref
{
"@odata.id": "https://graph.microsoft.com/v1.0/directoryObjects/{user-id}"
}
You can also add multiple members (up to 20 members can be added in a single request) to a group.
Use OData bind in a PATCH operation. PATCH https://graph.microsoft.com/v1.0/groups/{group-id}
{
"members@odata.bind": [
"https://graph.microsoft.com/v1.0/directoryObjects/{user-id-1}",
"https://graph.microsoft.com/v1.0/directoryObjects/{user-id-2}",
"https://graph.microsoft.com/v1.0/directoryObjects/{user-id-3}"
]
}
Configure the app to include the groups claims in the security tokens
To emit the group membership claims in security tokens, update the app. In the following JSON, replace the {App-ID} with your application ID (not object ID).
PATCH https://graph.microsoft.com/v1.0/applications(appId='{App-ID}')
{
"groupMembershipClaims": "SecurityGroup",
"optionalClaims": {
"idToken": [
{
"name": "groups",
"source": null,
"essential": false,
"additionalProperties": []
},
{
"name": "acrs",
"source": null,
"essential": false,
"additionalProperties": []
}
],
"accessToken": [
{
"name": "groups",
"source": null,
"essential": false,
"additionalProperties": []
},
{
"name": "acrs",
"source": null,
"essential": false,
"additionalProperties": []
}
],
"saml2Token": [
{
"name": "groups",
"source": null,
"essential": false,
"additionalProperties": []
}
]
}
}